Findings
- We examined the password policies of 120 of the most popular English-language websites in the world.
- We considered a website to be following best practices if it satisfied the following security and usability criteria:
- Security:
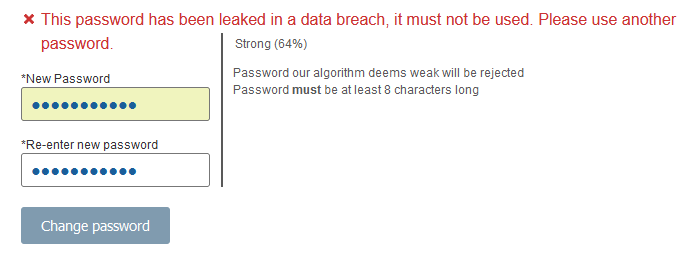
- Allowed 5 or fewer of the 40 most common leaked passwords and easiest-to-guess passwords (e.g., "12345678", "rockyou") we tried.
- Required passwords be no shorter than 8 characters OR employed a password strength meter that accurately measured a password's resistance to being guessed by an adversary.
- Usability: Did not impose any character-class requirements (e.g. "at least one digit and one special character").
- We found that only 15 websites were following best practices. The remaining 105 / 120 either leave users at risk for password compromise or frustrated from being unable to use a sufficiently strong password (or both).
Comparison of our key findings with best practices
| Interventions | Best practices from prior research | Our key findings |
|---|---|---|
|
Blocklists
|
|
|
|
Strength meters and minimum-strength requirements

|
|
|
|
Composition policies
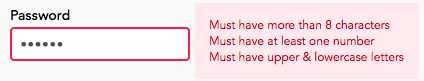
|
|
Paper/Data
Read the paper » Slides »For a breakdown of how each of the 120 websites fared on each of the criteria, see here.
We visited websites from October 2021 to December 2021. Researchers can download our data here, and view our call to research here.
Citation
@inproceedings{lee2022password,
author = {Kevin Lee and Sten Sj{\"o}berg and Arvind Narayanan},
title = {Password policies of most top websites fail to follow best practices},
booktitle = {Eighteenth Symposium on Usable Privacy and Security (SOUPS 2022)},
year = {2022},
isbn = {978-1-939133-30-4},
address = {Boston, MA},
pages = {561--580},
url = {https://www.usenix.org/conference/soups2022/presentation/lee},
publisher = {USENIX Association},
month = aug,
}